1.代理示例
对应的官方页面地址
以下是用户收集的不同反向代理配置示例列表。我们建议使用反向代理终止 TLS/SSL 连接(最好是 443 端口,即 HTTPS 的标准端口),而不是使用 Vaultwarden 内置的 HTTPS 功能。有关更多信息,请参阅启用 HTTPS。
在本文档中,我们假设您在与反向代理相同的主机上运行 Vaultwarden。如果您将 Vaultwarden 作为一个容器运行,假设您已经向主机发布了 -p 127.0.0.1:8000:80,因为容器内的 Vaultwarden 已经被配置为监听所有 IPv4 接口(ROCKET_ADDRESS=0.0.0.0)上的 80 端口(通过 ROCKET_PORT)。
示例还假定您没有加密反向代理和 Vaultwarden 之间的连接,即没有配置 ROCKET_TLS,因此反向代理可以直接通过 http://127.0.0.1:8000 连接到 Vaultwarden。
如果您使用 Docker Compose 将容器化的服务(例如,Vaultwarden 与反向代理)链接在一起,您必须调整示例代码以考虑到这一点(例如,将 127.0.0.1:8000 改为 service_name:80,而 service_name 通常是 vaultwarden)。请参阅使用 Docker Compose 了解这方面的示例。
可以使用 Mozilla 的 SSL Configuration Generator 来生成用于网页服务器的安全 TLS 协议和密码配置。已知所有受支持的浏览器和移动应用程序都可以使用这种「现代化的」配置。
Caddy 2.x
在大多数情况下 Caddy 2 会自动启用 HTTPS,参考此文档。
在 Caddyfile 语法中,{$VAR} 表示环境变量 VAR 的值。如果您喜欢,也可以直接指定一个值,而不是用一个环境变量的值来代替。
# 取消注释以下语句以及取消注释 import admin_redir 语句,以仅允许从本地网络访问管理界面
# {
# servers {
# trusted_proxies static private_ranges
# client_ip_headers X-Forwarded-For X-Real-IP
# # client_ip_headers CF-Connecting-IP X-Forwarded-For X-Real-IP
# # If using Cloudflare proxy, insert CF-Connecting-IP as first priority
# # since Cloudflare doesn't prevent X-Forwarded-For spoofing.
# }
# }
# (admin_redir) {
# @admin {
# path /admin*
# not remote_ip private_ranges
# }
# redir @admin /
# }
{$DOMAIN} {
log {
level INFO
output file {$LOG_FILE} {
roll_size 10MB
roll_keep 10
}
}
# 如果你想通过 ACME(Let's Encrypt 或 ZeroSSL)获获取证书,请取消注释
# tls {$EMAIL}
# 或者如果您提供自己的证书,请取消注释
# 如果您在 Cloudflare 后面运行,您也会使用此选项
# tls {$SSL_CERT_PATH} {$SSL_KEY_PATH}
# 此设置可能会在某些浏览器上出现兼容性问题(例如,在 Firefox 上下载附件)
# 如果遇到问题,请尝试禁用此功能
encode zstd gzip
# 取消注释以提高安全性(警告:只有在您了解其影响的情况下才能使用!)
# 如果您想使用 FIDO2 WebAuthn,请将 X-Frame-Options 设置为 "SAMEORIGIN",否则浏览器将阻止这些请求
# header / {
# # 启用 HTTP Strict Transport Security (HSTS)
# Strict-Transport-Security "max-age=31536000;"
# # 禁用 cross-site filter (XSS)
# X-XSS-Protection "0"
# # 禁止在框架内呈现网站 (clickjacking protection)
# X-Frame-Options "DENY"
# # 阻止搜索引擎建立索引(可选)
# X-Robots-Tag "noindex, nofollow"
# # 禁止嗅探 X-Content-Type-Options
# X-Content-Type-Options "nosniff"
# # 服务器名称移除
# -Server
# # 移除 X-Powered-By,虽然这不应该是一个问题,但最好移除
# -X-Powered-By
# # 移除 Last-Modified,因为 etag 相同并且同样有效
# -Last-Modified
# }
# 取消注释以仅允许从本地网络访问管理界面
# import admin_redir
# 取消注释以只允许从指定的转发 IP(例如 Cloudflare 代理)访问管理界面
# @not_allowed_admin {
# path /admin*
# Trusted IPs one and two
# not client_ip xx.xx.xx.xx/32 xx.xx.xx.xx/32
# # remote_ip's forwarded mode is deprecated; client_ip matcher with global options client_ip_headers and trusted_proxies
# }
# respond @not_allowed_admin "401 - {http.request.header.Cf-Connecting-Ip} is not an allowed IP." 401
# 将所有代理到 Rocket
# 如果位于子路径中,则 reverse_proxy 行将如下所示:
# reverse_proxy /vault/* 127.0.0.1:8000
reverse_proxy 127.0.0.1:8000 {
# 把真实的远程 IP 发送给 Rocket,以便 Vaultwarden 将其放入日志中,
# 这样 fail2ban 就可以阻止正确的 IP 了
header_up X-Real-IP {remote_host}
# 如果您使用 Cloudflare 代理,请将 remote_host 替换为 http.request.header.Cf-Connecting-Ip
# 如果使用全局选项 'client_ip_headers CF-Connecting-IP' 则不需要
# 请参阅 https://developers.cloudflare.com/support/troubleshooting/restoring-visitor-ips/restoring-original-visitor-ips/
# 以及 https://caddy.community/t/forward-auth-copy-headers-value-not-replaced/16998/4
}
}lighttpd (by forkbomb9)
erver.modules += ( "mod_proxy" )
$HTTP["host"] == "vault.example.net" {
$HTTP["url"] == "/notifications/hub" {
# WebSocket proxy
proxy.server = ( "" => ("vaultwarden" => ( "host" => "<SERVER>", "port" => 3012 )))
proxy.forwarded = ( "for" => 1 )
proxy.header = (
"https-remap" => "enable",
"upgrade" => "enable",
"connect" => "enable"
)
} else {
proxy.server = ( "" => ("vaultwarden" => ( "host" => "<SERVER>", "port" => 4567 )))
proxy.forwarded = ( "for" => 1 )
proxy.header = ( "https-remap" => "enable" )
}
}在 Vaultwarden 环境中,您必须将 IP_HEADER 设置为 X-Forwarded-For 而不是 X-Real-IP。
lighttpd with sub-path (by FlakyPi)
在这个示例中,通过 https://shared.example.tld/vault/ 访问 Vaultwarden。如果您想使用其他子路径,如 vaultwarden 或 secret-vault,则应更修改下面示例中的 vault 以匹配。
您还需要在 DOMAIN 环境变量的值中包含子路径(例如 DOMAIN: "https://shared.example.tld/vault"),才能使代理正常工作。
server.modules += (
"mod_openssl",
"mod_redirect"
)
$SERVER["socket"] == ":443" {
ssl.engine = "enable"
ssl.pemfile = "/etc/letsencrypt/live/shared.example.tld/fullchain.pem"
ssl.privkey = "/etc/letsencrypt/live/shared.example.tld/privkey.pem"
}
# Redirect HTTP requests (port 80) to HTTPS (port 443)
$SERVER["socket"] == ":80" {
$HTTP["host"] =~ "shared.example.tld" {
url.redirect = ( "^/(.*)" => "https://shared.example.tld/$1" )
server.name = "shared.example.tld"
}
}
server.modules += ( "mod_proxy" )
$HTTP["host"] == "shared.example.tld" {
$HTTP["url"] =~ "/vault" {
proxy.server = ( "" => ("vaultwarden" => ( "host" => "127.0.0.1", "port" => 8000 )))
proxy.forwarded = ( "for" => 1 )
proxy.header = (
"https-remap" => "enable",
"upgrade" => "enable",
"connect" => "enable"
)
}
}您必须将 Vaultwarden 环境配置中的 IP_HEADER 设置为 X-Forwarded-For 而不是默认的 X-Real-IP。
Nginx (by @BlackDex)
# 'upstream' 指令确保你有一个 http/1.1 连接
# 这里启用了 keepalive 选项并拥有更好的性能
#
# 此处定义服务器的 IP 和端口。
upstream vaultwarden-default {
zone vaultwarden-default 64k;
server 127.0.0.1:8000;
keepalive 2;
}
# 要支持 websocket 连接的话才需要
# 参阅:https://nginx.org/en/docs/http/websocket.html
# 我们不发送上述链接中所说的 "close",而是发送一个空值。
# 否则所有的 keepalive 连接都将无法工作。
map $http_upgrade $connection_upgrade {
default upgrade;
'' "";
}
# 将 HTTP 重定向到 HTTPS
server {
listen 80;
listen [::]:80;
server_name vaultwarden.example.tld;
return 301 https://$host$request_uri;
}
server {
# 对于旧版本的 nginx,在 ssl 后面的 listen 行中加入 http2,并移除 'http2 on'
listen 443 ssl;
listen [::]:443 ssl;
http2 on;
server_name vaultwarden.example.tld;
# 根据需要指定 SSL 配置
#ssl_certificate /path/to/certificate/letsencrypt/live/vaultwarden.example.tld/fullchain.pem;
#ssl_certificate_key /path/to/certificate/letsencrypt/live/vaultwarden.example.tld/privkey.pem;
#ssl_trusted_certificate /path/to/certificate/letsencrypt/live/vaultwarden.example.tld/fullchain.pem;
#add_header Strict-Transport-Security "max-age=31536000;";
client_max_body_size 525M;
location / {
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $connection_upgrade;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
# 如果您使用 Cloudflare 代理,请将 $remote_addr 替换为 $http_cf_connecting_ip
# 参阅 https://developers.cloudflare.com/support/troubleshooting/restoring-visitor-ips/restoring-original-visitor-ips/#nginx-1
# 或者使用 ngx_http_realip_module
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
location / {
proxy_pass http://vaultwarden-default;
}
# 除了 ADMIN_TOKEN 之外,还可以选择添加额外的身份验证
# 删除下面的 '#' 注释并创建 htpasswd_file 以使其处于活动状态
#
#location /admin {
# # 参阅:https://docs.nginx.com/nginx/admin-guide/security-controls/configuring-http-basic-authentication/
# auth_basic "Private";
# auth_basic_user_file /path/to/htpasswd_file;
#
# proxy_http_version 1.1;
# proxy_set_header Upgrade $http_upgrade;
# proxy_set_header Connection $connection_upgrade;
#
# proxy_set_header Host $host;
# proxy_set_header X-Real-IP $remote_addr;
# proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# proxy_set_header X-Forwarded-Proto $scheme;
#
# proxy_pass http://vaultwarden-default;
#}
}如果遇到 504 Gateway Timeout(网关超时)故障,可以通过在 server { 部分添加更长的超时时间来告诉 nginx 等待 Vaultwarden 的时间,例如:
proxy_connect_timeout 777;
proxy_send_timeout 777;
proxy_read_timeout 777;
send_timeout 777;Nginx with sub-path (by @BlackDex)
在这个示例中,Vaultwarden 的访问地址为 https://shared.example.tld/vault/,如果您想使用任何其他的子路径,比如 vaultwarden 或 secret-vault,您需要更改下面示例中相应的地方。
为此,您需要配置 DOMAIN 变量以使其匹配,它应类似于:
Nginx configured by Ansible/DebOps (by ypid)
使用 DebOps 配置 nginx 作为 Vaultwarden 的反向代理的清单示例。我选择在 URL 中使用 PSK 以获得额外的安全性,从而不会将 API 暴露给 Internet 上的每个人,因为客户端应用程序尚不支持客户端证书(我测试过)。 参考强化指南 - 隐藏在子目录下
Nginx (NixOS) (by tklitschi, samdoshi)
NixOS Nginx 配置示例。关于 NixOS 部署的更多信息,请参阅部署示例页面。
Nginx with proxy_protocol in front (by dionysius)
在这个例子中,有一个下游代理在这个 nginx 前面的 proxy_protocol 中进行通信(例如,启用了 proxy_protocol 的 LXD 代理设备)。Nginx 需要从这里设置正确使用协议和要转发的标头。标有 # <--- 的行与 blackdex 的示例内容不同。
参考这个 LXD 下游代理设备配置:
Apache (by fbartels)
请记得启用 mod_proxy_http,例如使用:a2enmod proxy_http。这要求 Apache >= 2.4.47。
如果您通过公共 https 地址访问您的密码库(服务器内部再将请求重定向到 http(例如 80 端口)),则必须启用 RequestHeader set X-Forwarded-Proto "https",否则,密码库虽然可以加载,但您的数据将无法加载。
Apache in a sub-location (by @agentdr8 & @NoseyNick)
修改 docker 启动以包含 sub-location。
请记得启用 mod_proxy_http,例如使用:a2enmod proxy_http。这要求 Apache >= 2.4.47。
Apache 2.4.47 (or later) in a sub-location (by @NoseyNick)
现在,常规的 mod_proxy 支持使用 upgrade=websocket 升级到 WebSocket,而不需要 mod_proxy_wstunnel。
复制上面的说明,除非使用更简单的...
HAproxy (by @BlackDex)
将这些行添加到您的 HAproxy 配置中。
HAproxy - before v1.29.0 (by @williamdes)
将这些行添加到您的 HAproxy 配置中。
HAproxy inside PfSense (by @RichardMawdsley)
作为 GUI 设置,下面的详细信息\说明供您在需要的地方添加。
假设您已经设置好了基本的 HTTP > HTTPS 重定向设置。基本设置
后端创建
后端 1:
后端 2:
前端创建-1-域名
ACCESS CONTROL LIST
ACTIONS-1-Domain
前端创建-2-VaultWarden
ACCESS CONTROL LIST
ACTIONS - 2 - VaultWarden
更新记录
重要提示
可选
完成!可以去做测试了!
反过来,可以将下面的等效项添加到您的配置中(请注意,这是一个示例摘要)。
为了进行测试,如果您在浏览器中导航到 /notifications/hub,那么您应该会看到一个页面,上面写着「WebSocket Protocol Error: Unable to parse WebSocket key.」(WebSocket 协议错误:无法解析 WebSocket 密钥。) ……这意味着它可以正常工作! - 所有其他子页面都应该出现 Rocket 错误。
HAproxy Kubernetes Ingress(by @devinslick)
控制器安装详情可在此处找到:https://www.haproxy.com/documentation/kubernetes-ingress/community/installation/on-prem/。请注意,仅当您使用 Cloudflare 时才需要 CF-Connecting-IP 标头
添加以下资源定义:
Istio k8s (by @asenyaev)
Istio k8s - before v1.29.0 (by @dpoke)
relayd on openbsd (by olliestrickland)
经测试可正常运行(包括 websockets) - /etc/relayd.conf - 在 openbsd 7.2 上使用来自 OpenBSD Ports 的 Vaultwarden - https://openports.se/security/vaultwarden
此配置取决于 tls 的正确设置 - 我使用 https://man.openbsd.org/acme-client
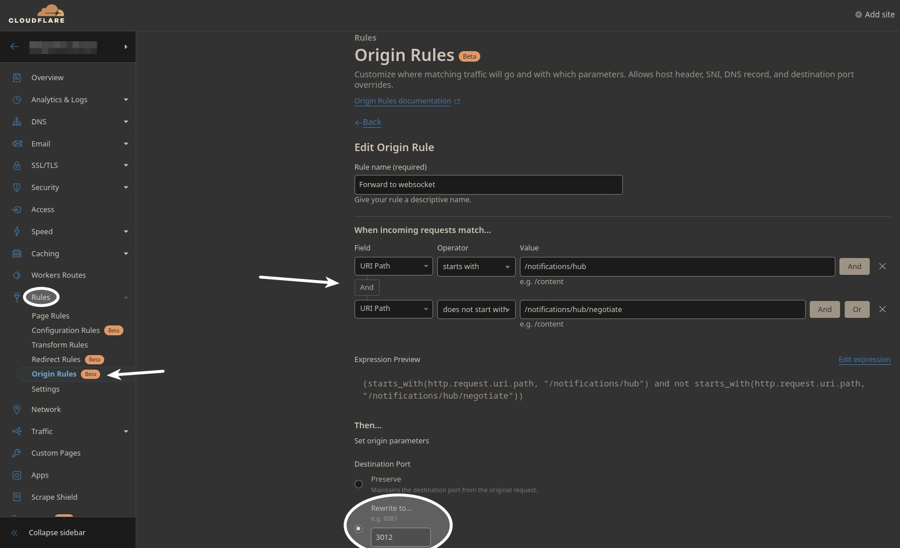
CloudFlare - before v1.29.0 (by @williamdes)
按照下面的截图创建新的规则。用于查找此设置的示例仪表板 URL:https://dash.cloudflare.com/xxxxxx/example.org/rules/origin-rules/new
CloudFlare Tunnel (by @calvin-li-developer)
docker-compose.yml:
cloudflared-config 文件夹中的内容:
请使用本指南找出您的 cloudflare 账户的以下内容/值。注意:aaaaa-bbbb-cccc-dddd-eeeeeeeee 只是一个随机的 tunnelID,请使用真实的 ID。
config.yml:
aaaaa-bbbb-cccc-dddd-eeeeeeeee.json:
最后更新于